Утилиты для удаления вирусов, троянов, червей, шпионских программ и другого вредоносного по (которое не видят антивирусы)
Содержание:
- How do I remove spyware?
- History of spyware
- Как Malware получает котроль над системой
- Возможности Malwarebytes Anti-Malware Free
- How can I tell if I have a malware infection?
- How do I protect myself from adware?
- Mobile spyware
- How can I tell if my Android device has malware?
- Beware of Greeks bearing gifts
- How do I prevent Trojans?
- Trojanized apps on Android smartphones
- ВИДЕО: Сотрудники МЧС взламывают дверь
- All about malware
- Types of adware
- Следы Malware в работе вашей системы
- How does malware affect my business?
- Источник угрозы
- Product Guide
- Do Macs get malware?
- Заключение
How do I remove spyware?
If your spyware infection is working as designed, it will be invisible unless you’re technically savvy enough to know exactly where to look. You could be infected and never know. But if you suspect spyware, here’s what to do.
- The first order of business is to make sure your system has been cleaned of any infection so that new passwords are not compromised. Get yourself a robust cybersecurity program with a reputation for aggressive spyware removal technology. Malwarebytes, for example, thoroughly cleans up spyware artifacts and repairs altered files and settings.
- After you have cleaned your system, think about contacting your financial institutions to warn of potential fraudulent activity. Depending on the compromised information on your infected machine, and especially if it is connected to a business or enterprise, you may be required by law to report breaches to law enforcement and/or make a public disclosure.
- If stolen information is sensitive in nature or involves the collection and transmission of images, audio, and/or video, you should contact local law-enforcement authorities to report potential violations of federal and state laws.
- One last thing: Many purveyors of identity theft protection advertise their services to monitor for fraudulent transactions, or to place a freeze on your credit account to prevent any form of activity. Activating a credit freeze is definitely a good idea. If you’re offered free identity theft monitoring as part of the settlement from a data breach, there’s no harm in signing up. However, Malwarebytes advises against purchasing identity theft protection.
“Many purveyors of identity theft protection advertise their services to monitor for fraudulent transactions…”
History of spyware
As with much Internet discourse, it’s difficult to pin down exactly where “spyware” as a word and a concept originated. Public references to the term date back to Usenet discussions happening in the mid-90s. By the early 2000s, “spyware” was being used by cybersecurity companies, in much the same way we might use the term today; i.e. some sort of unwanted software program designed to spy on your computer activity.
In June 2000, the first anti-spyware application was released. In October 2004, America Online and the National Cyber-Security Alliance performed a survey. The result was startling. About 80% of all Internet users have their system affected by spyware, about 93% of spyware components are present in each of the computers, and 89% of the computer users were unaware of their existence. Out of the affected parties, almost all, about 95%, confessed that they never granted permission to install them.
At present, and in general, the Windows operating system is the preferred target for spyware applications, thanks largely to its widespread use. However, in recent years spyware developers have also turned their attention to the Apple platform, as well as to mobile devices.
Как Malware получает котроль над системой
Для работы Malware требуется, чтобы пользователь его запустил, и это – только первый шаг. Достаточно часто Malware использует другие методы, чтобы предоставить себе наиболее вероятную гарантию хотя бы на единоразовый запуск в каждой из сессий работы системы
Для Malware исключительно важно производить запуск себя и резидентно присутствовать в памяти. И удобнее всего Malware прописываться при загрузке компьютера, а также при инициализации и переконфигурации системы
Основные места обитания Malware – файлы command.com, autoexec.bat и config.sys, файлы конфигурации в системах DOS и Windows при загрузке по стандартной схеме. Кроме того, часто Malware прячется в файлах главных шаблонов офисных приложений Word и Excel – Normal.dot и XLStart.
Возможности Malwarebytes Anti-Malware Free
- Удаление вредоносных программ как автоматически, так и в ручном режиме;
- Интеллектуальный эвристический анализ помогает удалять не явные вредоносные объекты;
- Программа обнаружения отличается качественными анти шпионскими модулями;
- В бесплатной версии, имеется встроенный блокировщик подозрительных веб-ресурсов;
- Быстрое сканирование системы с настраиваемым списком игнорирования;
- Реализована защита режиме реального времени — технология Real Time Protection;
- Способность работать в ускоренном режиме;
- Удаление вредоносного ПО в реальном времени;
- Эффективное помещение инфицированных файлов в карантин с последующей опцией восстановления.
Преимущества
- Поддерживается любая актуальная операционная система Windows, начиная от XP, Vista, заканчивая Windows 10;
- Антивирусная программа весьма быстро обнаруживает и удаляет вредоносные приложения;
- Современный и простой интерфейс, имеет русский язык оболочки;
- Возможность настройки для обеспечения максимально оптимизации и производительности;
- Отсутствуют какие-либо конфликты, если на ПК установлены другие антивирусы;
- Отличная система поиска и удаления червей, троянов и различного вредоносного программного обеспечения;
- Содержит передовую технологию Malwarebytes Chameleon, которая препятствует отключению антивируса сложными угрозами;
- В комплект с Malwarebytes Anti Malware Free Antivirus Software входят дополнительные утилиты;
- Антивирусные сканеры и базы сигнатур, стабильно обновляются с официального сайта Malwarebytes Corporation;
- Malwarebytes Anti Malware рекомендуют специалисты по информационной безопасности PC, Mac и других авторитетных ресурсов.
Недостатки
How can I tell if I have a malware infection?
Malware can reveal itself with many different aberrant behaviors. Here are a few telltale signs that you have malware on your system:
- Your computer slows down. One of malware’s main effects is to reduce the speed of your operating system,
whether you’re navigating the Internet or just using your local applications. - A tidal wave of annoying ads that shouldn’t be there washes over your screen. Unexpected pop-up ads are a
typical sign of a malware infection. They’re especially associated with a form of malware known as adware. What’s more, pop-ups usually come packaged with other hidden malware threats.
So if you see something akin to “CONGRATULATIONS, YOU’VE WON A FREE PSYCHIC READING!” in a
pop-up, don’t click on it. Whatever free prize the ad promises, it will cost you plenty. - Your system repeatedly crashes, freezes, or displays a BSOD (Blue Screen of Death), which can occur on Windows
systems after encountering a fatal error. - You notice a mysterious loss of disk space, probably due to a bloated malware squatter which hides in your hard
drive. - There’s a weird increase in your system’s Internet activity.
- Usage of your system resources is abnormally high and your computer’s fan starts whirling away at full
speed—signs of malware activity taking up system resources in the background. - Your browser’s homepage changes without your permission. Similarly, links you click send you to an unwanted
web destination. This usually means you clicked on that “congratulations” pop-up, which downloaded some
unwanted
software. Likewise, your browser might slow to a crawl. - New toolbars, extensions, or plugins unexpectedly populate your browser.
- Your antivirus product stops working and you cannot update it, leaving you unprotected against the sneaky malware
that disabled it. - Then there’s the painfully obvious, intentionally non-stealthy malware attack. This famously happens with
ransomware, which announces itself, tells
you it has your data, and demands a ransom to return your files. - Even if everything seems to be working just fine on your system, don’t get complacent, because no news
isn’t necessarily good news. Powerful malware can hide deep in your computer, going about its dirty business
without raising any red flags as it snags your passwords, steals sensitive files, or uses your PC to spread to
other computers.
How do I protect myself from adware?
Finally, even before all the above precautions, download a reputable cybersecurity program for your PC or mobile phone. Perform scans frequently, and keep your updates, well, up to date. Of course, we recommend any of our Malwarebytes family of anti-malware products as a prudent measure: Malwarebytes for Windows, Malwarebytes for Mac, Malwarebytes for Android, Malwarebytes for Chromebook, and Malwarebytes for iOS. By arming yourself with knowledge, and protecting yourself with a robust cybersecurity program, you can take the steps necessary for an adware-free life online.
See all our reporting on adware
at Malwarebytes Labs.
Mobile spyware
Also, it’s not just consumers that mobile spyware criminals target. If you use your smartphone or tablet in the workplace, hackers can turn their attack to your employer organization through vulnerabilities in mobile devices. Moreover, your corporation’s incident response team may not detect breaches that originate through a mobile device.
Spyware breaches on smartphones commonly occur in three ways:
- Unsecured free wi-fi, which is common in public places such as airports and cafes. If you log onto an unsecured network, the bad guys can see everything you do while connected. Pay attention to warning messages your device may give you, especially if it indicates that the server identity cannot be verified. Protect yourself by avoiding such unsecured connections.
- Operating system (OS) flaws, which open up exploits that could let attackers infect a mobile device. Smartphone manufacturers frequently release OS updates to protect users, which is why you should install updates as soon as they are available (and before hackers try to infect out-of-date devices).
- Malicious apps, which hide in seemingly legitimate applications, especially when they are downloaded from websites or messages instead of an app store. Here it’s important to look at the warning messages when installing applications, especially if they seek permission to access your email or other personal information. Bottom line: It’s best to stick to trusted sources for mobile apps and avoid any third-party apps.
How can I tell if my Android device has malware?
Fortunately, there are a few unmistakable red flags that wave at you if your Android phone is infected. You may be infected if you see any of the following:
- A sudden appearance of pop-ups with invasive advertisements. If they appear out of nowhere and send you to
sketchy websites, you’ve probably installed something that hides adware within it. So don’t click on
the ad. - A puzzling increase in data usage. Malware chews up your data plan by displaying ads and sending out the
purloined information from your phone. - Bogus charges on your bill. This happens when malicious software makes calls and sends texts to premium numbers.
- A disappearing battery charge. Malware is a resource burden, gulping down your battery’s juice faster than
normal. - People on your contact list report strange calls and texts from your phone. Malware replicates by spreading from
one device to another by means of emails and texts, inviting them to click on the infected link it displays. - A phone that heats up while performance lags. For instance, there’s even a Trojan out there that invades
Android phones with an installer so nefarious, that it can tax the processor to the point of overheating the phone,
which makes the battery bulge, and essentially leaves your Android for dead. - Surprise apps on your screen. Sometimes you download apps that have malware piggybacked onto them for a stealthy
installation. That happens because Android allows users to jump straight from Google Play to other marketplaces,
like Amazon, which might have let a malware maker slip through. - Your phone turns on WiFi and Internet connections on its own. This is another way malware propagates, ignoring
your preferences and opening up infection channels. - Further down, we’ll touch upon what you should do if your Android is infected. Plus, here’s a Malwarebytes blog article on securing your privacy on an Android.
Beware of Greeks bearing gifts
In Virgil’s epic poem, The Aeneid, a clever Greek war strategist named Odysseus devises a plan to get his men inside the walled city of Troy. Instead of destroying or climbing the city’s walls, Odysseus sees another way in: with deception. Trojan soldiers watch as the Greeks appear to sail away, leaving behind a giant wooden horse as a token of surrender. Drunk on victory, the Trojans bring the horse inside their walls, only to discover Odysseus and his men were hidden inside the whole time.
Like its namesake, Trojan horse attacks, or simply “Trojans” use deception and social engineering to trick unsuspecting users into running seemingly benign computer programs that hide malicious ulterior motives.
How do I prevent Trojans?
Since Trojans rely on fooling users into letting them into the computer, most infections are avoidable by remaining vigilant and observing good security habits. Practice a healthy skepticism about websites offering free movies or gambling, opting instead to download free programs directly from the producer’s site rather than from unauthorized mirror servers.
Another precaution to consider: change the default Windows settings so that the real extensions of applications are always visible. This avoids getting tricked by an innocent looking icon.
Other good practices besides installing Malwarebytes for Windows, Malwarebytes for Android, and Malwarebytes for Mac include:
- Running periodic diagnostic scans
- Setting up automatic updates of your operating system software, ensuring you have the latest security updates
- Keeping your applications updated, ensuring any security vulnerabilities are patched
- Avoiding unsafe or suspicious websites
- Being skeptical of unverified attachments and links in unfamiliar emails
- Using complex passwords
- Staying behind a firewall
Trojanized apps on Android smartphones
Trojans aren’t just a problem for laptops and desktops. They attack mobile devices as well, which makes sense given the tempting target presented by the billions of phones in use.
As with computers, the Trojan presents itself as a legitimate program, although it’s actually a fake version of the app full of malware.
Such Trojans usually lurk on unofficial and pirate app markets, enticing users to download them. The Trojans run the full gamut of mischief, infecting the phone with ads and keyloggers, which can steal information. Dialer Trojans can even generate revenue by sending out premium SMS texts.
“Browser extension add-ons can act as Trojans as well….”
Android users have been the victims of Trojanized apps even from Google Play, which is constantly scanning and purging weaponized apps (many times after the Trojan’s discovery). Browser extension add-ons can act as Trojans as well, since it’s a payload capable of carrying embedded bad code.
While Google can remove browser add-ons from computers, on phones the Trojans can place transparent icons on the screen. It’s invisible to the user, but nonetheless reacts to a finger touch to launch its malware.
As for iPhone users, there’s good news: Apple’s restrictive policies regarding access to its App Store, iOS, and any other apps on the phone do a good job of preventing Trojan incursions. The only exception occurs for those who jailbreak their phones in their quest to download freebies from sites other than the App Store. Installing risky apps outside the Apple settings makes you vulnerable to Trojans.
ВИДЕО: Сотрудники МЧС взламывают дверь
All about malware
You know how every year the medical community campaigns for everyone to get a flu shot? That’s because flu
outbreaks typically have a season—a time of year when they start spreading and infecting people.
In contrast, there are no predictable seasonal infections for PCs, smartphones, tablets, and enterprise networks.
For them, it’s always flu season. But instead of suffering chills and body aches, users can fall ill from a
kind of machine malady—malware.
Malware infections come at us like a torrent of water from a fire hose, each with its own methods of attack—from
stealthy and sneaky to subtle like a sledgehammer. But if knowledge is power, as a preventative inoculation against
infection, we offer here a short course on malware, what it is, its symptoms, how you get it, how to deal with it,
and how to avoid it in the future.
Types of adware
For all the ways adware tries to dig into your PC or other device, most adware strategies qualify as browser
hijackers. These interlopers specialize in modifying Internet browser settings without the user’s knowledge
or consent. Typically, hijackers change the homepage and default search settings. You’re happily surfing
along when suddenly the ads start pummeling you. You might naturally assume that the ads originate from the site
you’re visiting, but they aren’t. But since they appear in the form of pop-ups or pop-unders, they seem
that they are embedded in the site itself.
Once again, there are adware programs that change your start page, your search engine, or even fiddle with the
shortcuts on your computer that open your browsers. There is also, of course, different adware for different
devices and operating systems. So you might have to cope with mobile/Android adware, Mac adware, or Windows adware.
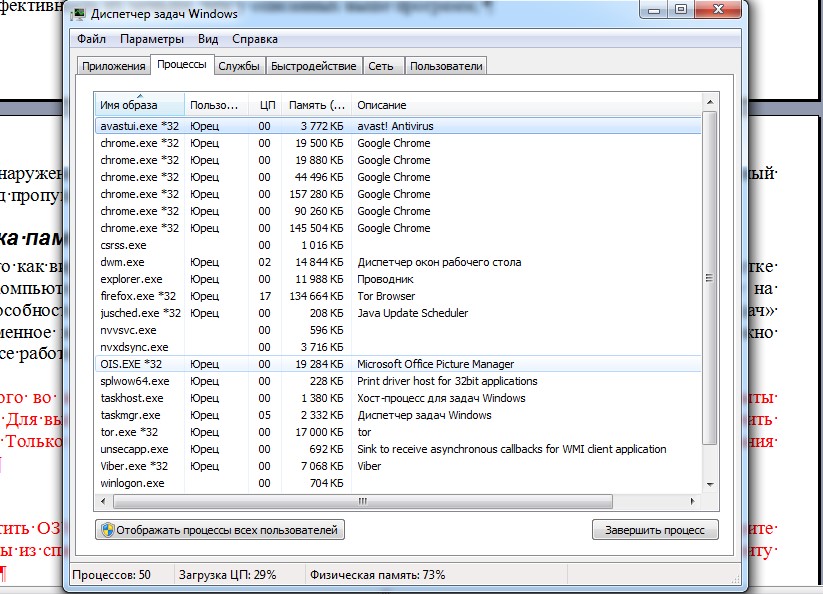
Следы Malware в работе вашей системы
- Невозможность изменять настройки браузера. Для того, чтобы у вас не было возможности поменять параметры браузера, которые заданы Malware программой, некоторые из них совсем удаляют или нарушают возможность изменения в меню инструментов и на панели управления параметров браузера. Если вы делаете попытку изменить домашнюю страницу вашего браузера, и у вас это не получается, то скорее всего — это «проделки» Malware.
- Не запускается антивирусная программа. Эта же причина мешает вам открыть и запустить антивирус или другой сервис, который обеспечивает безопасность системы компьютера.
- Всплывающие окна при отсутствии интернет-подключения. Еще одним из главных признаков того, что у вас на компьютере есть зловредное программное обеспечение, является всплывающие окна и объявления, даже если ПК работает автономно.
How does malware affect my business?
Malware attacks on businesses went up 55 percent in the second half of 2018 with banking Trojans and ransomware proving to be the most popular types of attacks. Specifically, Trojan attacks on businesses rose 84 percent while ransomware attacks went up 88 percent.
So why are cybercriminals bullish on business attacks? The answer is simple: businesses present a broader attack surface and more bang for the buck. In one noteworthy example, the Emotet banking Trojan hobbled critical systems in the City of Allentown, PA, requiring help from Microsoft’s incident response team to clean up and racking up remediation costs to the tune of $1 million.
In another example, the SamSam ransomware brought the City of Atlanta to its knees by taking down several essential city services—including revenue collection. Ultimately, the SamSam attack cost Atlanta $2.6 million to remediate.
While Emotet and SamSam grab the headlines, the majority of ransomware cases as of late have been the result of GandCrab. First detected in January of 2018, the GandCrab ransomware has already gone through several iterations as its authors try to avoid detection and strengthen encryption. It’s been estimated GandCrab has already netted its authors somewhere around $300 million in paid ransoms, with individual ransoms set from $600 to $700,000.
Considering the tremendous cost associated with a malware attack, and the current rise of ransomware and banking Trojans in particular, here’s some tips on how to protect your business from malware.
- Implement network segmentation. Spreading your data onto smaller subnetworks reduces your attack surface—smaller targets are harder to hit. This can help contain a breach to only a few endpoints instead of your entire infrastructure.
- Enforce the principle of least privilege (PoLP). In short, give users the access level they need to do their jobs and nothing more. Again, this helps to contain damages from breaches or ransomware attacks.
- Backup all your data. This goes for all the endpoints on your network and network shares too. As long as your data is archived, you can always wipe an infected system and restore from a backup.
- Educate end users on how to spot malspam. Users should be wary of unsolicited emails and attachments from unknown senders. When handling attachments, your users should avoid executing executable files and avoid enabling macros on Office files. When in doubt, reach out. Train end users to inquire further if suspicious emails appear to be from a trusted source. One quick phone call or email goes a long way towards avoiding malware.
- Educate staff on creating strong passwords and implement some form of multi-factor authentication (MFA)—two-factor authentication at a bare minimum.
- Patch and update your software. Microsoft releases security updates the second Tuesday of every month and many other software makers have followed suit. Stay in the loop on important security updates by subscribing to the Microsoft Security Response Center blog. Expedite the patch process by launching updates at each endpoint from one central agent, as opposed to leaving it up to each end user to complete on their own time.
- Get rid of end of abandonware. Sometimes it’s hard to get rid of old software that’s past its expiration date—especially at a large business where the purchasing cycle moves with the urgency of a sloth, but discontinued software is truly the worst-case scenario for any network or system administrator. Cybercriminals actively seek out systems running outdated and obsolete software so replace it as soon as possible.
- Get proactive about endpoint protection. Malwarebytes, for example, has multiple options for your business with Endpoint Protection and Endpoint Detection and Response.
Источник угрозы
Самые опасные и сложные вредоносные программы создаются на заказ государственными спецслужбами или связанными с ними группами киберпреступников. Такие объекты имеют ярко выраженную специфику и направлены на конкретную жертву или группу жертв. Целью их работы могут быть сбор и кража секретных данных либо прямое вредительство.
Однако большинство вредоносных программ создается рядовыми злоумышленниками, не связанными с организованной киберпреступностью или спецслужбами. Внедрив свои разработки на компьютер жертвы, они могут красть данные для доступа к счетам в банках, выполнять с зараженного устройства сетевые атаки, вымогать выкупы, размещать рекламу сомнительной продукции или рассылать спам. Источником распространения вредителей являются мелкие преступники, похищающие логины, пароли и другую личную информацию (например, аккаунты участников онлайн-игр) с целью несанкционированного использования или продажи.
Внедрять вредоносные программы могут исследователи, находящиеся в процессе изобретения иных способов заражения, противодействия антивирусным продуктам. Цель деятельности этих программистов состоит не в получении выгоды, а в изучении компьютерной среды и проверке своих идей.
Product Guide
Do Macs get malware?
Conventional wisdom has sometimes held that Macs and iPads are immune to catching viruses (and don’t need an antivirus). For the most part, that’s true. At the very least, it hasn’t happened
in a long time.
“Mac systems are subject to the same vulnerabilities (and subsequent symptoms of infection) as Windows
machines and cannot be considered bulletproof.”
Other kinds of malware are a different story. Mac systems are subject to the same vulnerabilities (and subsequent
symptoms of infection) as Windows machines and cannot be considered bulletproof. For instance, the Mac’s
built-in protection against malware doesn’t block all the adware and spyware bundled with fraudulent
application downloads. Trojans and keyloggers are also threats. The first detection of ransomware written
specifically for the Mac occurred in March 2016, when a Trojan-delivered attack affected more than 7,000 Mac users.
In fact, Malwarebytes saw more Mac malware in 2017 than in any previous year. By the end of 2017, the number of new
unique threats that our professionals counted on the Mac platform was more than 270 percent higher compared to the
number noted in 2016.
For more on the state of Mac malware, visit the Malwarebytes blog site here.
Заключение
Единственное о чем я хочу вас предупредить — не стоит скачивать подозрительные программы и приложения, которые обещают расширить функционал ВК. Многие из них могут привести к взлому вашего аккаунта (см. взлом страницы вк). Поэтому лучше использовать проверенные варианты.
Вопросы?
Пожалуйста, задайте свой вопрос в комментариях, с описанием возникшей проблемы
Мы и наши пользователи, регулярно обсуждаем возможные неполадки и сложности. Вместе мы разберемся с Вашей проблемой.